In today’s hyper-connected world, data is a top commodity – one prized by both governments and criminals. With social media and the news shaping our opinions and beliefs, information gathered from individuals is priceless.
Targeted advertising monitors your behavior to better understand your preferences in order to suggest more relevant advertising. Social media platforms like Facebook and Instagram collect your data to develop a profile of you as a consumer and an individual.
From the Cambridge Analytica scandal, it is clear that data willingly provided by millions of social media users are being harvested for nefarious purposes.
From shifting your beliefs to influencing your decisions, it’s clear that the information age is turning into a dystopian nightmare. One where every word is monitored, analyzed and then manipulated back to you.
This is why data encryption has an increasingly larger role in today’s world. Protecting your data and ensuring that the wrong parties do not gain access to sensitive information is key.
What does encrypted message mean?
In a nutshell, encryption refers to the process of converting data into another form prior to it being transferred. This data can then only be unlocked with the use of a specialized digital key that decrypts the information into a recognizable form.
Encrypted messages have been around since the dawn of time with its roots in warfare. During the time of the Roman Empire, generals would use specialized ciphers to communicate with one another.
This ensured that in the event that a messenger was captured, vital strategic information would not be made available to the enemy as they lacked the proper cipher to decrypt the message.
World War II is another clear example of the importance role that message encryption has. By encrypting their messages with their Enigma machine, German commanders were able to coordinate crippling u-boat raids on British shipping.
Left unchecked, this could be disastrous for Britain and her allies who were heavily reliant on merchant vessels to deliver vital supplies. As the Allies were unable to decrypt German messages, they were helpless to protect their shipping lines.
However, the Allies would gain the upper-hand with the breaking of the German Enigma code. Something which allowed them to decipher German encrypted messages and counter their u-boat raids.
The same concept can be applied to sending text messages nowadays. Encrypted text messages are nearly impossible to intercept and decipher which goes a long way towards protecting your privacy.
End-to-end encryption explained
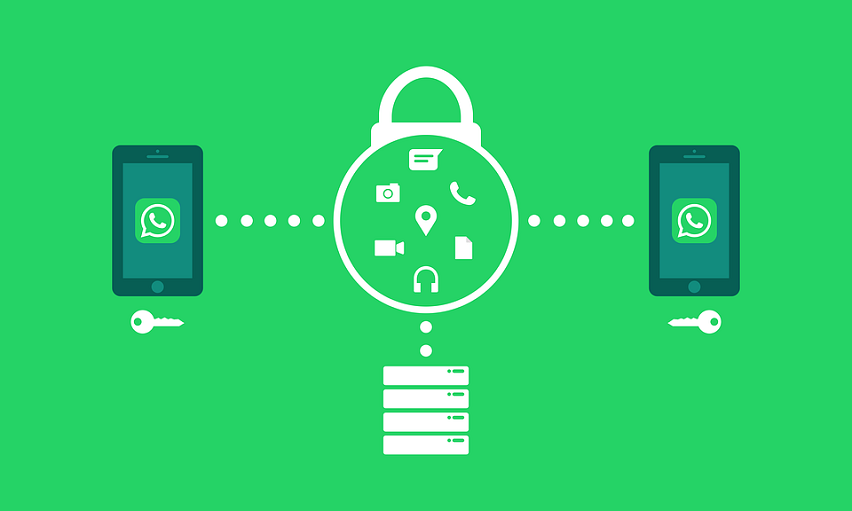
End-to-end encryption or E2EE uses cryptography to encode messages for security purposes. This ensures that parties outside that of the recipient are not able to decipher the contents of the message.
To do so, E2EE systems utilize what is known as cryptographic keys to both encode and decipher the contents of a message. Any party that does not have the correct decryption key will find it nearly impossible to gain access to an encrypted message.
Cryptographic keys stored at the end point makes it nearly impossible for conventional hackers to intercept said messages. This system is not foolproof however with two known key weaknesses.
Firstly, a hacker could theoretically gain access to encrypted messages by stealing the public key of either one or both endpoints. This would enable them to perform a man-in-the-middle attack thus gaining access to sensitive information.
Secondly, developments in technology and computing power could allow a dedicated hacker to perform a brute force attack to break the encryption key.
Both situations are worrisome which is why researchers are constantly working on ways to further improve E2EE technology.

Why is SMS messaging outdated?
Also known as short message service, SMS has been one of the simplest yet most effective methods of communication since the development of mobile phones. SMS allows a person to quickly communicate with a friend or loved one via text messages.
Given the massive volume of text messages sent on a daily basis, the odds of a hacker actually intercepting and reading your message are abysmal. This is however, no reason to remain complacent.
In fact, by taking a closer look, it is clear to see that SMS messaging is woefully outdated. Being the world’s most popular OS, Android is used by potentially billions of users around the globe everyday.
With the exception of third-party applications, Android does not encrypt text messages sent from a phone. Even with the support of third-party software, the effectiveness of such apps remains highly doubtful.
The lack of message encryption also means that text messages sent via mobile present a major security risk. This is because unencrypted text messages leak metadata such as telephone numbers which can lead to the identification of the sender.

Why Should You Use an Encrypted Messaging App?
Encrypted messaging apps emerged in response to the revelation that both government bodies and private companies have a vested interest in harvesting the data of consumers.
Messenger apps employ sophisticated message encryption technology. This provides an additional layer of security that makes it all the more difficult for your messages to be read.
Encrypted messaging apps also reduce the likelihood of you becoming a victim of cybercrimes such as fraud and identity theft. It is shocking how most phone users choose to exchange sensitive financial information via SMS. This provides hackers and thieves with the perfect opportunity to steal and misuse such delicate information.
Message encryption: what to encrypt?
1. The connection
Encrypting your internet connection is an easy and effective way to safeguard your identity whilst protecting your privacy. Virtual private networks or VPNs encrypt your online traffic by routing your it through various servers.
This ensures that your internet browsing experience remains private and protects you from being tracked.
2. Your actual email messages
Emails contain a variety of sensitive information that can be stolen or used against you. Encrypting this text ensures that parties with malicious intent will not be able to gain access to this information.
3. Your stored, cached, or archived email messages
From financial statements to confidential personal details such as medical records, it’s always good practice to encrypt stored, cached, or archived email messages. As can be seen by the controversy involving emails sent by former secretary of state Hillary Clinton, old emails can still cause plenty of trouble.
How Secure Is Your Recipient?
While you may have taken steps to safeguard yourself. You will still need to ask yourself how secure your recipient actually is. Have you taken steps to identify their identity?
Has a thorough evaluation of their cybersecurity protocols been conducted?
Failing to conduct the proper due diligence can result in the failure of even the most secure of systems.
Make sure you always follow the proper measures to have a safe browsing online and avoid using public wi-fi networks.